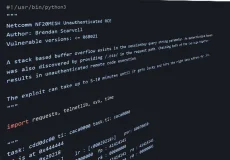
CVE-2024-3094 - xz/liblzma backdoor starting with version 5.6.0

backdoor in upstream xz/liblzma leading to ssh server compromise
CVE-2024-3094 Detail
Archlinux - The xz package has been backdoored
All servers have already been updated and tested. Everything is fine.
If you use Arch, test it as follows:
ldd /usr/sbin/sshd | grep -e libsystemd -e liblzmaIf ssh is linked with libsystemd/liblzma, as is the case with Debian, libsystemd.so.0 => /lib/x86_64-linux-gnu/libsystemd.so.0 and liblzma.so.5 => /lib/x86_64-linux-gnu/liblzma.so.5, then you should take a closer look at this! Debian stable for example is running 5.4.1, which is fine, if you have sid enabled you are most likely affected. Just check your distributions for any news regarding this vulnerability. libsystemd can be linked to liblzma. So if you only have libsystemd, be on the safe side and check your distribution for news there too.
There are also scripts to test your system that can give you a false alarm on Arch, such as https://raw.githubusercontent.com/cyclone-github/scripts/main/xz_cve-2024-3094-detect.sh .
The latest version of Arch is 5.6.1-2, so still 5.6.1, but without the security hole.
Edit:
Collection of specific distro links.
Have a good Easter
Dan